Cloud security posture management (CSPM) automates the identification and remediation of risks across cloud infrastructures spanning across Infrastructure as a Service (IAAS), Software as a Service (SAAS) & Platform as a Service (PAAS). CSPM tools empower companies to identify and remediate risks through security assessments and automated compliance monitoring. After moving to the cloud, many organizations mistakenly assume their cloud hosting provider is entirely responsible for security. This mistaken belief leads to data breaches and other security mishaps.
Over the course of a day hundreds & thousands of transactions connect & disconnect within the cloud infrastructure from outside or within the organization. This dynamic nature makes clouds powerful, but it also makes them hard to secure and as a cloud-first philosophy becomes the norm, the problem of securing cloud-based systems becomes more acute.
WHY TRADITIONAL SECURITY TOOLS & SOLUTIONS DON’T WORK IN THE CLOUD
- Lack of Perimeter to protect
- Traditional security needs to move & adapt at the ever-increasing speed of Cloud.
- Unable to provide visibility adding to confusion & misconfigurations.
- No adherence to Industry regulations while organization constantly evolves & adopts first-to-market approach.
While cloud-based computing delivers overall cost benefits, the security piece of that puzzle can eat into the ROI, as there are so many pieces that need to be managed – microservices, containers, Kubernetes, serverless functions, etc. The infamous cybersecurity skills gap is highly relevant here, as new technologies are rolling out faster than enterprises can find security professionals who have experience working for them.
Today’s enterprise environments are large and complex, making it difficult to track and maintain tens of thousands of resources and accounts. Permissions set by developers might be too liberal and they might even lose track of Crown Jewels leading to misconfigurations. Misconfigurations can happen easily, and often by accident. Misconfigurations are often caused by the mismanagement of multiple connected resources like Kubernetes, serverless functions and containers.
"95 percent of all security breaches are due to misconfigurations, and those mistakes cost companies nearly $5 trillion in between 2018 and 2019 alone" - Gartner
Underlying all of these issues is the greatest challenge of all: lack of visibility. With the proliferation of cloud resources, many organizations are unaware of how many cloud assets are running and how they’re all configured. This lack of visibility can cause misconfigurations to go undetected for days, weeks or even months, making it harder to secure the applications. Cloud environments have become too large and complex for enterprises to rely on manual assessment tools leading way for automation as the only solution.
WHY NGS:
- Continuously monitor and assess Industry regulatory compliances
- Continuous compliance validation will help in detecting and resolving compliance violations by utilizing Cloudbots.
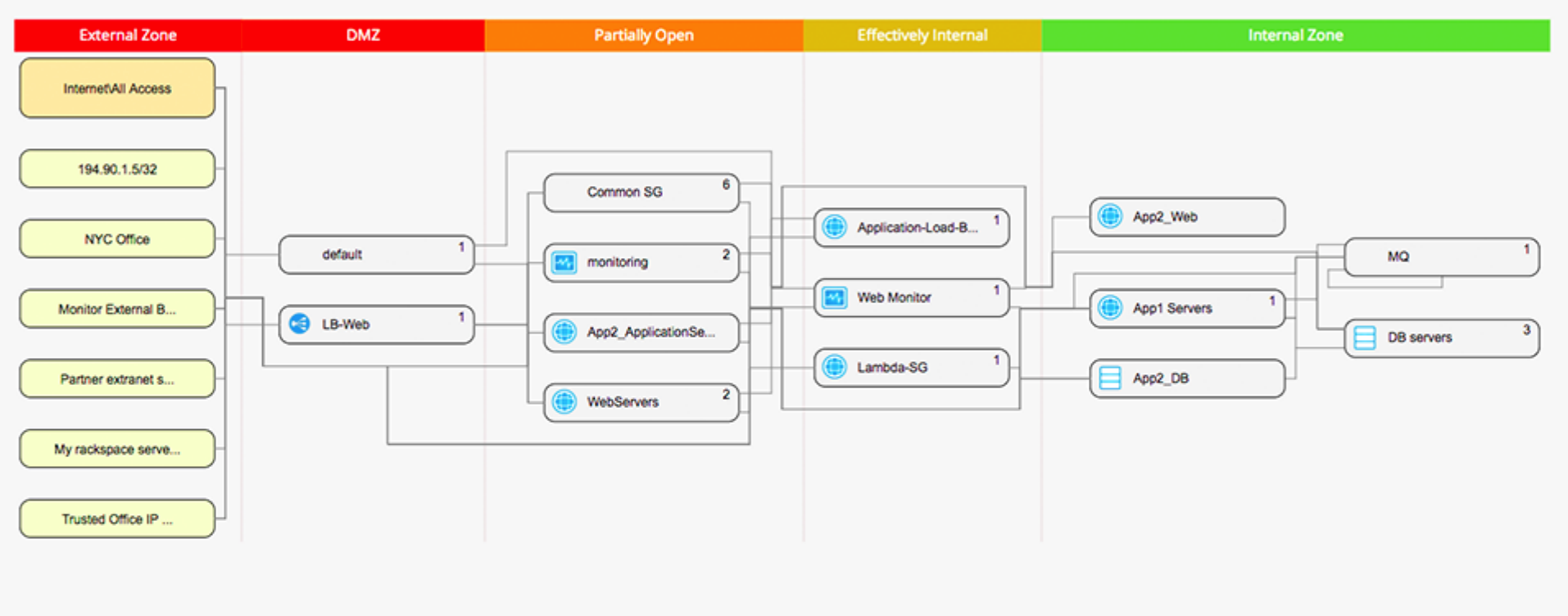
- Visualize cloud Infrastructure
- Identify how new assets are inter-connected and what policies or traffic routes to deploy
- Manage incident response
- Centrally review how threats are being detected, quarantined, and remediated.
- Employ Identity Access Management
- On -time access helps avoid misuse of privileges by conjoining authentication with authorization.
- Classify Cloud assets
- Deployment to cloud assets in designated region to ensure adherence to compliance and local data residency laws.
Adopting a cloud security posture management solution is the best way for any organization to secure their cloud infrastructure and keep data secure. Issues are easier to resolve when continuous monitoring, automation, and proper configuration are applied.