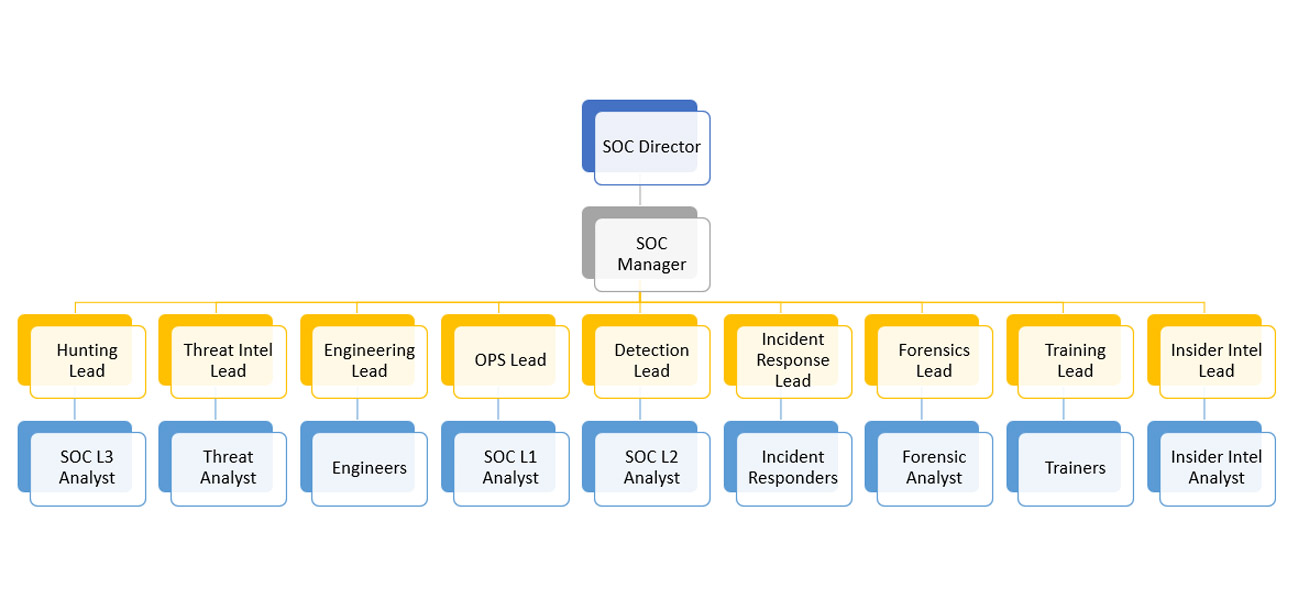
SOC Manager
Defines the vision for the entire team, owns the budget and resource allocation. Acts as the bridge to the rest of the business, championing the SOC's value to the wider organization.
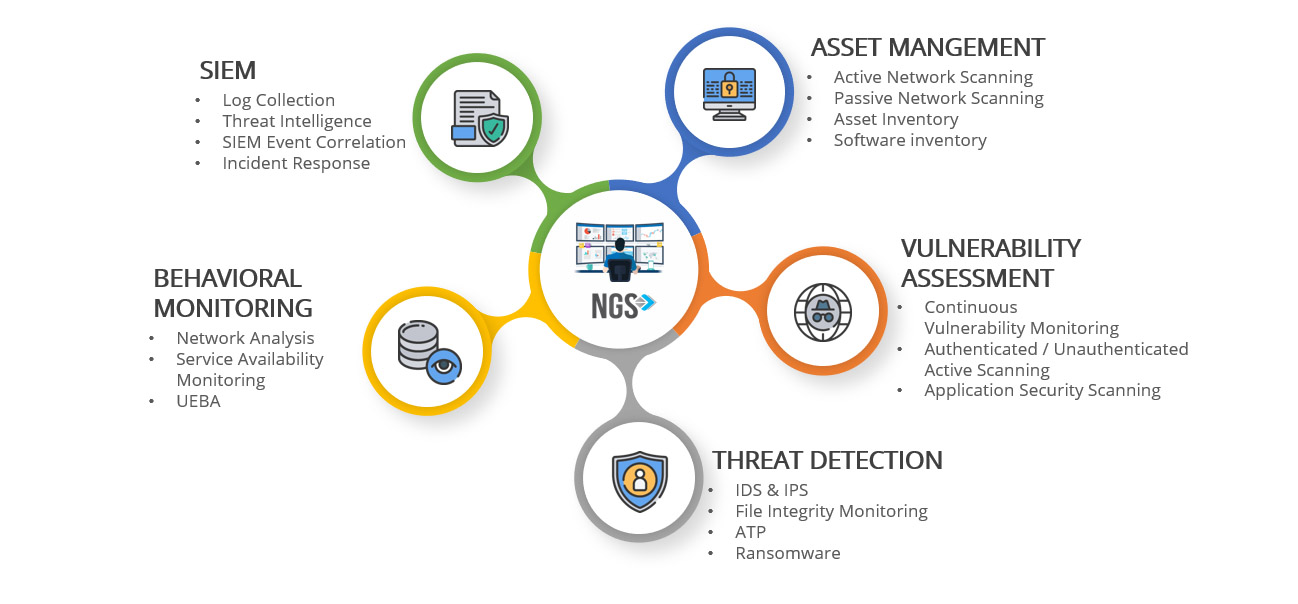
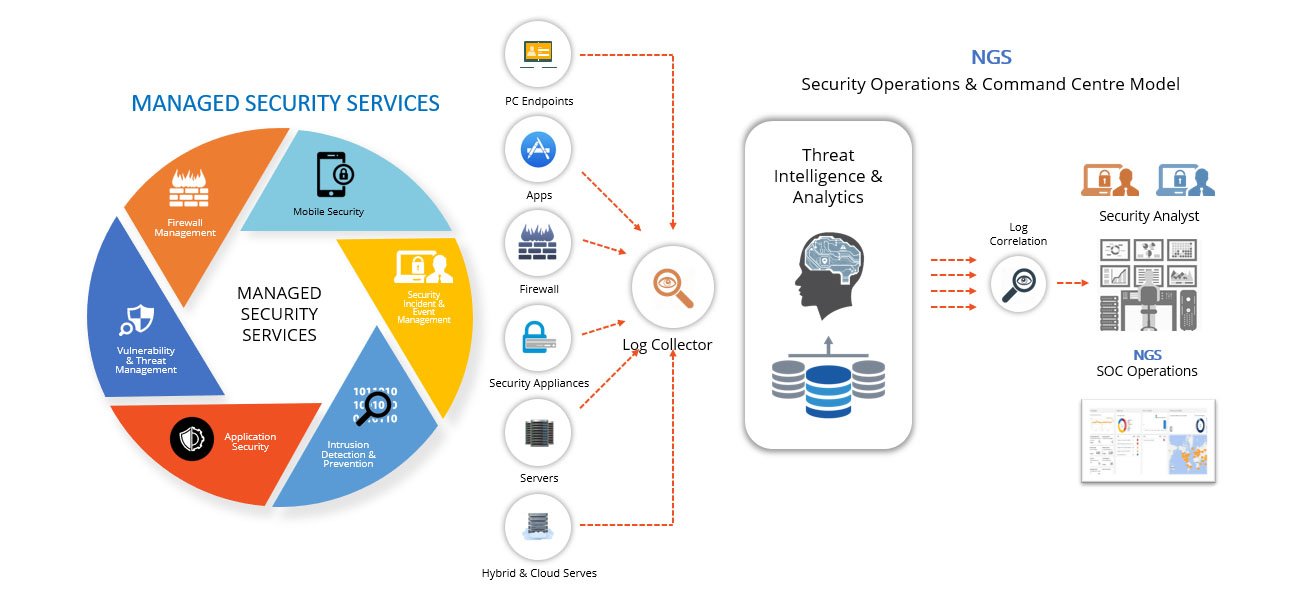
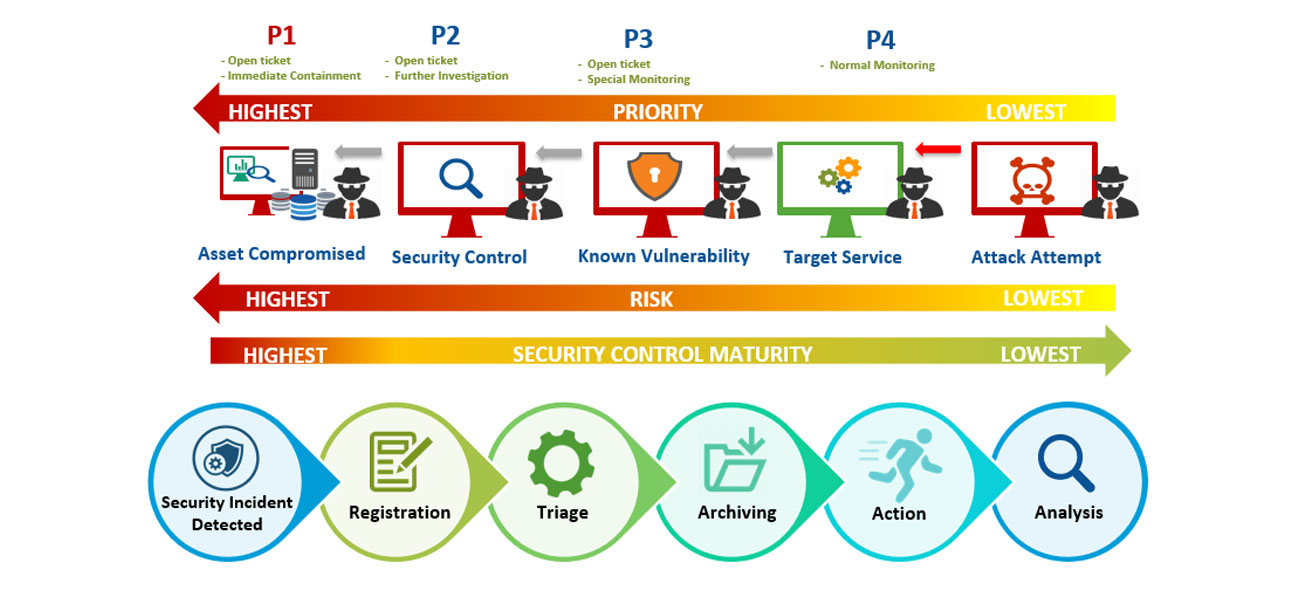
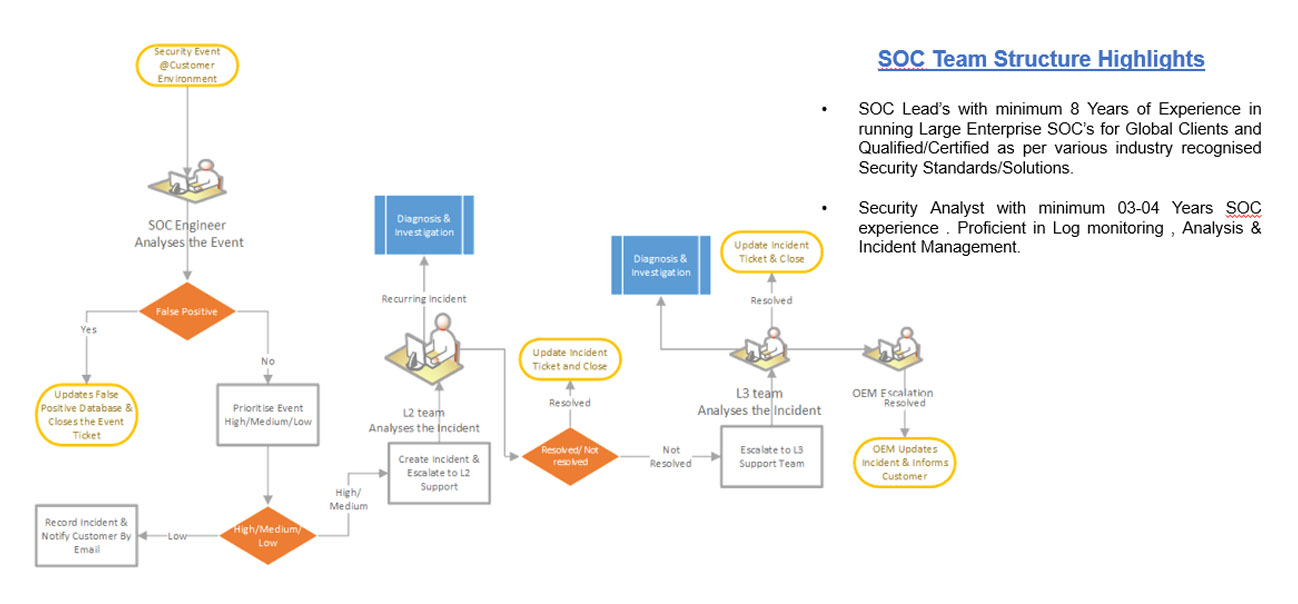
Defines the vision for the entire team, owns the budget and resource allocation. Acts as the bridge to the rest of the business, championing the SOC's value to the wider organization.
This role demands a big picture view -coordinating responses to threats through to effectively managing team members. They run the operations of the SOC on a hands-on basis.
This "eyes on glass role" is the front line, actively monitoring the system for suspicious activity and determining threat severity and complexity.
Combats higher levels of threats and conducts deep-dive investigations to identify affected systems, reviews intelligence reports and identifies the nature of an attack.
Security Information and Event Management (SIEM) Engineers fine-tune, configure and maintain the SIEM tools needed to identify and repel threats.
Threat hunters are the detectives in the team. They'll use SIEM tools to review log files (in realtime), finding clues as to the nature of the attack and how to repel it.
Remediates security incidents and focuses on containing and repelling attacks and repairs affected systems.
This person detects the nature of the threat to identify its origin and form and then passes intelligence to the SIEM Engineer who in turn feeds it into the system.
Conducts thorough investigations into the nature of the attack. Intelligence gathered is often shared with authorities and used as a basis to prevent future attacks.
Actively attacks the system to identify vulnerabilities. Using ethical hacking techniques, they'll use pen-tests to highlight weak areas so other teammates can fix them.